Filters
Stock royalty-free photos and images of Luka w zabezpieczeniach
Discover unlimited high resolution images of Luka w zabezpieczeniach and stock visuals for commercial use.

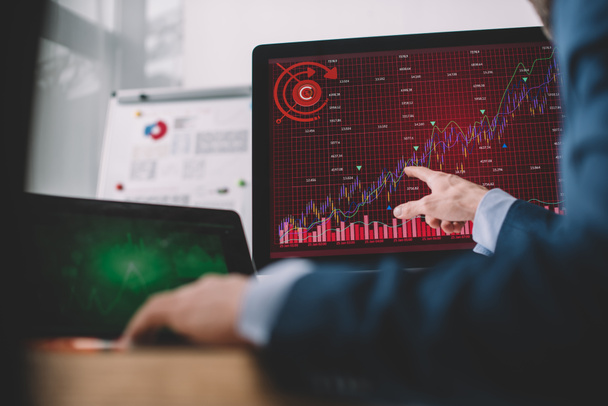
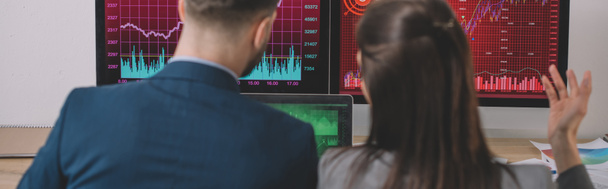
Security button pointing the highest position with two fingers, Conceptual image for risk management

Hack security Data protection. Computer Internet safe with lock, key on microscheme chip. Concept image of security vulnerability and information leaks

Safety computer security concept. Internet protection symbol on blured keyboard background. Concept image of security vulnerability and information leaks

Vulnerable encryption and cyber security shows an open key lock on a black smartphone for hacker attack or cyber attack protection as safety in business and consumer market against hacker activities

Safety computer security concept. Internet protection symbol on blured keyboard background. Concept image of security vulnerability and information leaks

Cyber security lock. Security computer Data Internet protection symbol on blured keyboard background. Concept image of security vulnerability and information leaks

CPU under umbrella, 3D rendering isolated on white background

The magnifying glass is a concept in antivirus software that has identified potential danger in a hidden digital code. 3d illustration.

Text showing inspiration Cross Site Scripting, Business concept Security vulnerability mainly found in web application Two Professional Well-Dressed Corporate Businessmen Handshake Indoors
Writing displaying text Cross Site Scripting, Word Written on Security vulnerability mainly found in web application Athletic Man illustration Mountain Proud Of Climbing Success To The Clouds Sky.

Conceptual hand writing showing Cross Site Scripting. Concept meaning Security vulnerability mainly found in web application Hands on Keyboard Front White Monitor with Screen Protector

Handwriting text Cross Site Scripting, Business showcase type of security vulnerability that can be found in some web applications

Writing displaying text Cross Site Scripting, Business concept type of security vulnerability that can be found in some web applications

Text caption presenting Cross Site Scripting, Concept meaning Security vulnerability mainly found in web application Editing Website Program Codes, Learning New Programming Language

Conceptual display Cross Site Scripting, Business overview Security vulnerability mainly found in web application Hand Holding Jigsaw Puzzle Piece Unlocking New Futuristic Technologies.

Writing note showing Cross Site Scripting. Business concept for Security vulnerability mainly found in web application

Conceptual hand writing showing Cross Site Scripting. Concept meaning Security vulnerability mainly found in web application

Inspiration showing sign Cross Site Scripting, Concept meaning type of security vulnerability that can be found in some web applications

Hand writing sign Cross Site Scripting, Business idea Security vulnerability mainly found in web application Editing Website Program Codes, Learning New Programming Language

Word writing text Cross Site Scripting. Business photo showcasing Security vulnerability mainly found in web application Empty tag blank space colorful background label rectangle attached string

Word writing text Cross Site Scripting. Business photo showcasing Security vulnerability mainly found in web application Man and Woman in Business Suit Presenting Report of Check and Lines on Paper

Text showing inspiration Cross Site Scripting, Conceptual photo Security vulnerability mainly found in web application Four Colleagues Illustration Having Conversations Brainstorming New Ideas.

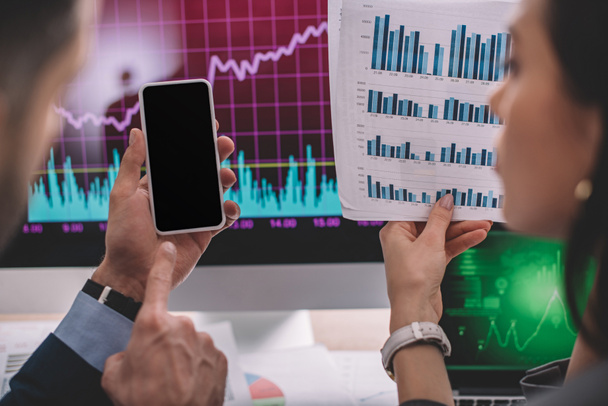
Text sign showing Cross Site Scripting. Business photo text Security vulnerability mainly found in web application Businessman Hand Touching Pointing to Bar Line Chart on Smartphone Screen

Smartphone in hand Security Vulnerability Log4J. Security vulnerability Log4j. The concept of cyber crime, cybersecurity and information security incidence. Cyber attack and crime.
Trusted Platform Module, TPM with like icon, 3D rendering isolated on white background

Male executive drawing a risk assessment diagram

Computer security breach close up

Credit card data encryption security lock
Finger clicking on a display with a lock icon. HUD display showing stages of hacking in progress: exploiting vulnerability, executing and Granted Access

Devastated female hacker after trying to hack a firewall and get access denied.

Cyber safety concept, lock and key on computer keyboard close-up

Mysterious hacker gaining unauthorized access into government system, doing phishing for security breach. Planting virus and malware to exploit computer server, illegal access. Handheld shot.

Excited hacker team after access granted on a cyber attack. Cybercrime.

Cyber security concept background: input password

Privacy Security Password SSL Background Image Illustration Blue

Open security lock on computer keyboard - computer security breach concept

Cyber security concept background with padlocks

Hand holding a security lock computer security concept

Master key or Gold Padlock on electronic motherboards background in concept of cyber security.

Cellphone data security - lock and phone on white

Computer security breach due to worm attack with closed lock

Master key or Gold Padlock on electronic motherboards background in concept of cyber security.

Padlock with chain on a laptop computer keyboard. Cyber security abstract concept. Vertical orientation.

Hacker leader helping girl with her hacking using a dangerous virus.

Credit card phishing attack security concept

Cyber security concept background with padlock

Closeup metal security lock with password on computer keyboard, security double lock concept in computer

Cyber criminal wearing a white mask while testing government system. Cyber hacker.

Security lock on white computer keyboard - computer security breach concept

Online shopping concept with padlock open locked with cipher on laptop beside money cards. Non secure online shopping concept.