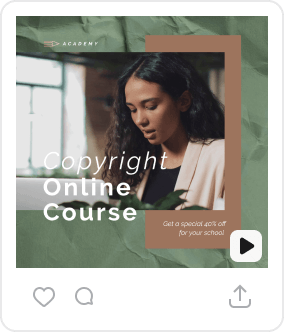
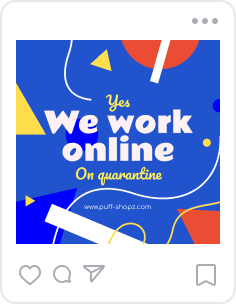
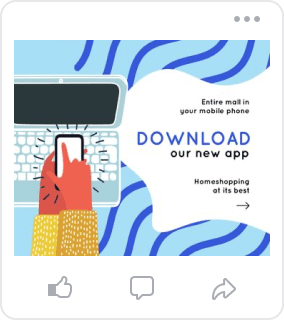
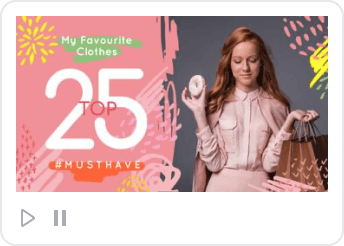
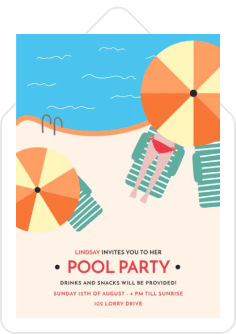
Similar Royalty-Free ImagesFile ID:195230020ByEdZbarzhyvetsky

Man hacker programmer using laptop on dark background

Islamic terrorist getting instructions of attack via internet, financing online

A man in a mask prints on the keyboard at a table in the dar

A man in a mask prints on the keyboard at a table in the dar

A man in a mask prints on the keyboard at a table in the dar

Hacker in the hood working with laptop typing text in dark room. Data security concept. Image with glitch effect

Hacker in a hood stealing information with computer on dark background

A man in a mask prints on the keyboard at a table in the dar

Hacker using the computer, young man using the computer, programmer with lines of code, hacking

A hacker in a hood and glasses is sitting at the keyboard and looking strangely at the camera, on a black background

Women hacker breaks into government data servers and Infects Their System with a Virus at his hideout place has dark blue atmosphere, Lady hooded using laptop on binary code background

Hacker using the computer, young man using the computer, programmer with lines of code, hacking

Hacker using the computer, young man using the computer, programmer with lines of code, hacking

A man in a mask prints on the keyboard at a table in the dar

Hacker in black mask and hood at the table in front of the monito

Man in hoodie is hacking personal data. Information security. Protection of information concept. Bad password.

Women hacker breaks into government data servers and Infects Their System with a Virus at his hideout place has dark blue atmosphere,

Hacker in the black hood in a room with wooden walls makes cybercrime

Portrait of a cyber hacker stealing information using a computer. Cybercrime and data security concept.

Women hacker breaks into government data servers and Infects Their System with a Virus at his hideout place has dark blue atmosphere, Lady hooded using laptop on binary code background

A man in a mask prints on the keyboard at a table in the dar

A man in a mask prints on the keyboard at a table in the dar

Man wear clothes look like hacker and sit with arm-crossed in room also in front of monitor show light with sign look fear and scary. Concept of safety for computor system and danger with hacker.

Hacker in black mask and hood at the table in front of the monito

Hacker man making a computer attack starting to typing on laptop keyboard and breaking password Male engaging hacking into security systems Freelancer using laptop cyber crime. High quality 4k footage

Christmas Candle Burning on The Table. Close-up

Hacker in black mask and hood at the table in front of the monito

The computer hacker working in dark room

A man in a mask prints on the keyboard at a table in the dar

The Mannequin and laptop in dark tone for cyber crime content.

Hacker blue colored with binary background

Professional hacker with computer keyboard sitting at table on dark background

Hacker use laptop

Islamic terrorist hacking board computers to have complete control over plain

Portrait of a cyber hacker stealing information using a computer. Cybercrime and data security concept.

Hacker in a hood in a dark room, the intruder breaks into a system, the concept of web crimes

A man in a mask prints on the keyboard at a table in the dar

Hacker in black mask and hood at the table in front of the monito

Picture of male hacker stealing on internet

A man in a mask prints on the keyboard at a table in the dar

Hacker with laptop initiating cyber attack, isolated on black backgroung

Hacker in a hood stealing information with computer on dark background

Hacker in the black hood in a room with wooden walls makes cybercrime

Terrorist making timebomb. terrorism and dangerous concept. Dark background

Hacker in black mask and hood at the table in front of the monitor

Hacker in the black hood in a room with wooden walls makes cybercrime

Hacker in the black hood in a room with wooden walls makes cybercrime

Anonymous hacker and face mask with smartphone in hand. Man in black hood shirt trying to hack personal data from mobile phone. Represent cyber crime data hacking or personal data stealing concept.

Blurry imagr Hacker in front of his computer face mask Hooded computer hacker stealing financial information and fake news with a laptop.

Brussels, Belgium - September 16, 2022: Hooded identity theft wearing an Anonymous Guy Fawkes mask

A man in a mask prints on the keyboard at a table in the dar

Anonymous Hacker with computer on colorful dark background

Hacker with laptop initiating cyber attack, isolated on black backgroung

Hacker in black mask and hood at the table in front of the monitor

Hacker in hoodie using laptop and looking into camera with evil eyes, malware

A man in a mask prints on the keyboard at a table in the dar

Silhouette of a hacker with laptop on table

Hacker in black mask and hood at the table in front of the monito

Portrait of mature bearded hipster man working overtime in the living room at home late at night in the dark

A man in a mask prints on the keyboard at a table in the dar

Hacker in black mask and hood at the table in front of the monito

Hacker in the office with headphones with microphone in search of prey. Steals data and copy of Bank from His Underground Hideout

Cyber hacker breaks into databases to obtain information using a computer. Cybercrime and data security concept.

A photo of two hackers who are speaking during a videoconference

Anonymous computer hacker in white mask and hoodie. Obscured dark face with keyboard computer in the dark. Data thief, internet attack, darknet and cyber security concept.

Hacker in black mask and hood at the table in front of the monito